Tim, Ptolemy Group, Inc - Owner | VP
The Shortcomings of ISP-Supplied Networking Equipment
In the current digital era, where cyber threats not only evolve with alarming sophistication but also pose significant risks to businesses, the imperative for robust network security has never been more critical. This detailed examination brings to light the considerable risks associated with the reliance on Internet Service Provider (ISP)-supplied modem/router combos for business networks. It strongly advocates for a paradigm shift towards network setups managed by cybersecurity professionals, emphasizing the indispensable role of Managed Security Service Providers (MSSPs) such as PDS, a recognized Gold WatchGuard Partner, in deploying advanced firewall solutions like WatchGuard to bolster security.
Limited Security Features and Customization
The inherent limitations in the security features and customization options of ISP-supplied networking devices starkly contrast with the diverse and complex security requirements of modern businesses. A 2021 study by cybersecurity firm Kaspersky revealed that 70% of router models on the market exhibited vulnerabilities, with a significant number of these devices supplied by ISPs. This finding highlights the inadequacy of a “one-size-fits-all” approach and underscores the necessity for businesses to gain full control over their networking hardware for tailored security configurations.
(Cite: https://www.kaspersky.com/about/press-releases/2022_87-critical-vulnerabilities-discovered-in-routers-in-2021 )
Outdated Firmware and Vulnerabilities
The potential for outdated firmware in ISP-supplied devices poses a significant threat, leaving networks susceptible to cybercriminal exploitation. The discovery of the “Cable Haunt” vulnerability in 2020 affected millions of cable modems globally, including those provided by ISPs, allowing attackers to execute arbitrary code on the devices. This and other similar incidents emphasize the urgent need for businesses to ensure their networking equipment is kept up-to-date with the latest security patches.
(Cite: https://www.securityweek.com/cable-haunt-millions-cable-modems-broadcom-chips-vulnerable-attacks/ )
Double NAT Complications and Privacy Concerns
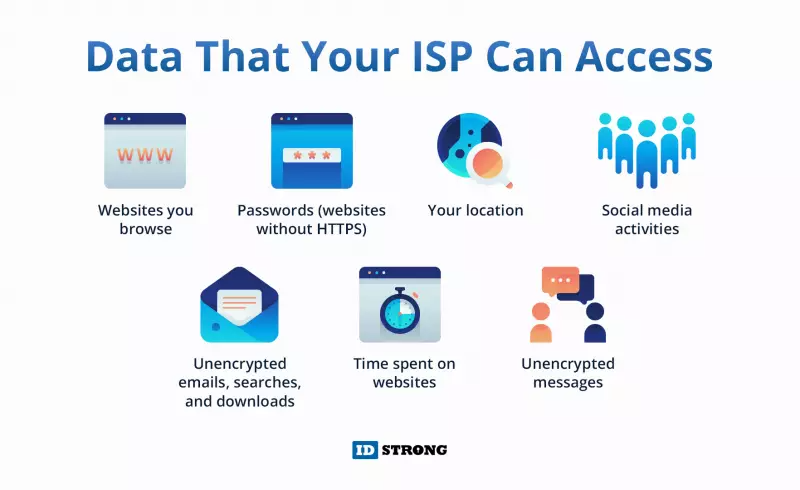
Adding to the complexity, the employment of additional networking equipment alongside ISP-supplied routers often results in double NAT setups, leading to connectivity issues and hindering the use of essential services like VoIP and VPNs. Moreover, a Cisco report from 2021 shed light on how these configurations complicate secure remote work, elevating the risk of cyber incidents. The potential for ISPs to access devices and the data they handle further exacerbates privacy and security concerns, spotlighting the critical need for secure and private network configurations.
(Cite: https://www.cisco.com/c/dam/global/en_uk/products/security/pdf/cisco-emea-report-2020_fa_final.pdf )
The Imperative for Professional Cybersecurity Management
Specialized Expertise
Navigating the labyrinth of modern cybersecurity threats necessitates specialized knowledge and expertise. The SolarWinds Orion breach of late 2020, a sophisticated supply chain attack affecting thousands of organizations, serves as a poignant reminder of the complexity of current cyber threats. This incident underscores the value of having certified IT professionals and cybersecurity experts who are equipped to design, implement, and manage an effective security infrastructure.
(Cite: https://www.securityweek.com/cable-haunt-millions-cable-modems-broadcom-chips-vulnerable-attacks/ )
Dedicated Firewalls: A Critical Defense Mechanism
The critical role of dedicated firewalls in protecting against cyber threats was dramatically underscored by the Colonial Pipeline ransomware attack in May 2021. This breach, initiated through a compromised password, illustrates how advanced security features of dedicated firewalls, such as stateful and deep packet inspection, intrusion detection and prevention systems, and real-time threat intelligence, are essential for scrutinizing network traffic and preemptively mitigating threats.
(Cite: https://www.cisa.gov/news-events/news/attack-colonial-pipeline-what-weve-learned-what-weve-done-over-past-two-years )
Leveraging MSSP Expertise and Advanced Firewall Solutions
The incorporation of managed firewall solutions from MSSPs offers a decisive advantage in the cybersecurity battleground. A notable success story involves a major healthcare provider that, in early 2022, effectively countered an advanced persistent threat (APT) attack thanks to the cutting-edge WatchGuard firewall technologies provided by their MSSP. This incident exemplifies how the latest in firewall technology, supported by the profound expertise of seasoned cybersecurity professionals, can safeguard businesses from emerging threats.
Regulatory Compliance and Cybersecurity Insurance: The Role of Dedicated Firewalls
In today’s digital landscape, adhering to regulatory compliances such as the Federal Trade Commission (FTC) guidelines, Health Insurance Portability and Accountability Act (HIPAA), and standards for electronic Protected Health Information (ePHI), among others, is crucial for businesses. These regulations underscore the importance of implementing robust cybersecurity measures, including dedicated perimeter firewalls, to protect sensitive data and ensure privacy. Moreover, cybersecurity insurance policies often stipulate the need for dedicated firewalls to qualify for coverage, highlighting their essential role in compliance and risk management strategies.
FTC Compliance
The FTC mandates that businesses safeguard consumer information against unauthorized access and threats. While the FTC does not specify the use of dedicated firewalls explicitly, its guidance underlines the necessity for protective measures that can be effectively provided by dedicated firewalls. The FTC’s Safeguards Rule, part of the Gramm-Leach-Bliley Act, requires financial institutions to design, implement, and maintain safeguards to protect consumer information, implicitly advocating for robust network security measures like dedicated firewalls.
HIPAA and ePHI Standards
HIPAA compliance is critical for healthcare entities that handle ePHI. The HIPAA Security Rule explicitly requires covered entities to implement technical safeguards to protect ePHI that is created, received, maintained, or transmitted electronically. Among these safeguards, the requirement for a “firewall” is interpreted as necessitating dedicated firewalls to ensure the integrity and confidentiality of ePHI. For instance, section 164.312(e)(1) of the HIPAA Security Rule mandates the protection of electronic information across open networks, which dedicated firewalls adeptly provide.
Cybersecurity Insurance Requirements
Cybersecurity insurance policies increasingly mandate the implementation of dedicated firewalls as part of their underwriting criteria. Insurers recognize that businesses with dedicated firewalls are better equipped to defend against cyber threats, reducing the risk of costly breaches and data loss incidents. For example, a cybersecurity insurance policy might stipulate specific network security practices, including the use of dedicated firewalls, as prerequisites for coverage eligibility. This ensures that insured entities adhere to best practices in cybersecurity, aligning with insurers’ risk management strategies.
Regulatory compliances and cybersecurity insurance requirements highlight the indispensable role of dedicated firewalls in safeguarding sensitive data and ensuring network security. By adhering to FTC guidelines, HIPAA standards for ePHI, and cybersecurity insurance criteria, businesses demonstrate their commitment to robust cybersecurity practices. Implementing dedicated firewalls not only helps entities meet regulatory and insurance compliance but also fortifies their defenses against the ever-evolving landscape of cyber threats, ensuring the protection of sensitive information and the integrity of their digital infrastructure.
Conclusion
The reliance on ISP-supplied modem/router combos, fraught with vulnerabilities and limitations, severely compromises business security. Transitioning to professionally managed network setups, complemented by the expertise of certified IT professionals, and fortified through advanced security measures provided by MSSPs like PDS, is crucial. By adhering to FTC guidelines, HIPAA standards for ePHI, and cybersecurity insurance criteria, businesses demonstrate their commitment to robust cybersecurity practices. Implementing dedicated firewalls not only helps entities meet regulatory and insurance compliance but also fortifies their defenses against the ever-evolving landscape of cyber threats, ensuring the protection of sensitive information and the integrity of their digital infrastructure. By transitioning to network setups professionally managed by certified IT professionals and fortified with the advanced security measures offered by MSSPs like PDS, businesses can substantially elevate their cybersecurity posture. This strategic approach not only addresses immediate security needs but also lays the foundation for long-term resilience, ensuring comprehensive protection for business data and infrastructure. Moreover, adherence to regulatory compliances and meeting cybersecurity insurance criteria further solidify the commitment to a secure digital ecosystem, maintaining operational integrity, customer trust, and success in the digital age. Such a commitment to cybersecurity is not merely strategic but essential for maintaining operational integrity, customer trust, and the broader success in today’s increasingly digital landscape.
Can you afford to not Check that box on Cyber Security Insurance forms? Can your business afford to put your data and customers data at risk with ISP Supplied Devices?