Tim, Ptolemy Group, Inc - Owner | VP
Phishing scams continue to be a persistent and highly effective form of cyberattacks in today’s digital landscape. Recognizing the peril they present to businesses, it is of paramount importance to comprehend how threat actors exploit phishing emails.
Within this blog, you will gain insight into the motivations driving phishing emails, the various incarnations of phishing attacks, and, most critically, strategies for safeguarding your email and business.
The Objectives of Phishing Emails
Phishing emails serve as the bait with which cybercriminals seek to entice unsuspecting victims into actions that can disrupt business operations, such as money transfers, divulging passwords, downloading malware, or exposing sensitive data. The core objective of a phishing assault revolves around monetary theft, data theft, or often both.
Monetary Theft: The most prevalent goal of a phishing endeavor is to steal funds. Scammers employ diverse tactics, such as Business Email Compromise (BEC), to execute fraudulent money transfers or employ ransomware to extort funds.
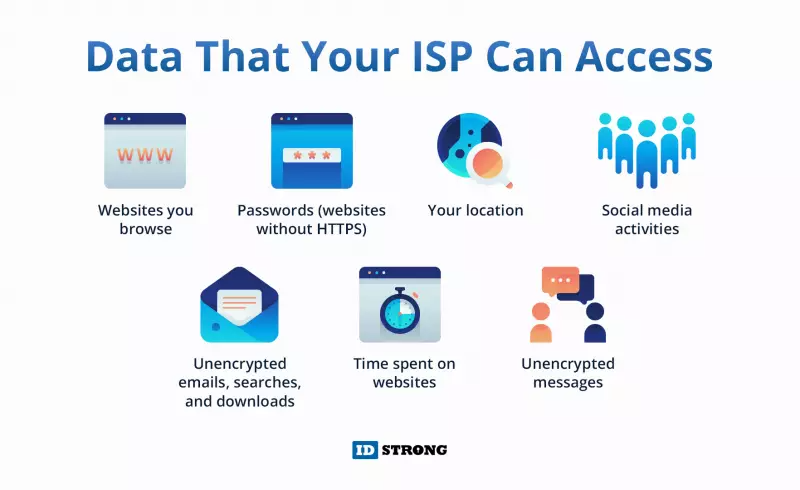
Data Theft: For cybercriminals, the value of your data, encompassing usernames, passwords, identity data like social security numbers, and financial information such as credit card numbers or bank account details, is immeasurable. This data can be used to perpetrate financial thefts or inject malware. Furthermore, your sensitive data may be sold on the dark web for financial gain.
Remaining Vigilant Against Phishing Attempts:
- Exercise caution when confronted with emails prompting you to click on a link, as they may conceal malicious software capable of pilfering your data and personal information.
- Be wary of emails directing you to a website, as they may lead to malicious sites designed to steal your personal information, including login credentials.
- Maintain alertness when an email contains an attachment, as deceptive extensions disguised as documents, invoices, or voicemails can infect your computer and pilfer personal information.
- Exercise skepticism when pressured into immediate actions, such as fund transfers, by an email. Verify the authenticity of such requests prior to taking any action.
Diverse Phishing Variants:
It is essential to recognize that phishing attacks are continually evolving and can target businesses of all sizes. While phishing emails are a common avenue for cybercriminals, they also exploit text messages, voice calls, and social media messages. Here are various types of phishing traps to remain cautious of:
- Spear Phishing: Cybercriminals send highly personalized emails targeting individuals or businesses to coerce them into sharing sensitive information, including login credentials or credit card details. Spear phishing emails may also serve as vehicles for distributing malware.
- Whaling: A subset of spear phishing, whaling targets high-ranking executives. Perpetrators impersonate trusted sources or websites in an attempt to steal information or money.
- Smishing: An increasingly popular cyberattack, smishing employs text messages masquerading as communications from trusted sources to manipulate victims into sharing sensitive information or making financial transfers.
- Vishing: Cybercriminals resort to vishing, or voice phishing, by making phone calls while posing as individuals from organizations such as the IRS, banks, or the victim’s workplace. The primary aim of voice phishing is to extract sensitive personal information.
- Business Email Compromise (BEC): BEC constitutes a spear phishing attack that employs a seemingly legitimate email address to deceive the recipient, often a senior-level executive. The primary objective of a BEC scam is to persuade an employee to transfer funds to the cybercriminal while masquerading as a legitimate, authorized business transaction.
- Angler Phishing: Also referred to as social media phishing, this scam primarily targets social media users. Cybercriminals with fraudulent customer service accounts deceive disgruntled customers into revealing their sensitive information, including bank details. Frequently, the targets are financial institutions and e-commerce enterprises.
- Brand Impersonation: Known as brand spoofing, this phishing scheme employs emails, texts, voice calls, and social media messages to impersonate renowned businesses. Cybercriminals dupe customers of these businesses into divulging sensitive information. While brand impersonation chiefly targets customers, it can also tarnish a brand’s reputation.
Strengthening Email Security:
Emails serve as a lifeline for your business, but implementing best email practices and safety standards can be a daunting task. Therefore, it is prudent to consider partnering with an IT service provider like PDS. We possess the requisite resources and tools to fortify your business against cyberattacks, allowing you to focus on essential tasks without anxiety. Reach out to us today!